Our team offers deep technical knowledge and consultative expertise to help you identify and deploy the right Transcend solutions for your projects. From embedded memory to enterprise SSDs and industrial-grade storage, we work closely with you to ensure seamless integration and long term reliability across every application.
Whether you need guidance during the design-in phase or advice on lifecycle management, our dedicated pre-sales and commercial teams are here to support you with end-to-end service. With full access to Transend’s custom services, product roadmap insights, and post-sale technical support, we help you deliver secure, stable, and failure-ready solutions to your customers.
Transcends Solid-State drive (SSD) solutions offer fast and reliable performance in a wide variety of form factors, interfaces and storage capacities suitable for devices operating in extreme industrial conditions. With support for Transcend Power Shield, Dynamic Thermal Throttling and S.M.A.R.T analysis technologies, our SSDs are designed for durability and reliability in large-scale embedded deployments.
From first signal to containment in minutes, not hours. We don’t just alert, you get real action.
Connect all your systems, ingest unlimited data, and scale as you grow. No hidden fees, no surprises.
Mapped reporting for NIS2, DORA, Cyber Essentials Plus, ISO27001 and more, making audits and regulatory requirements easy.

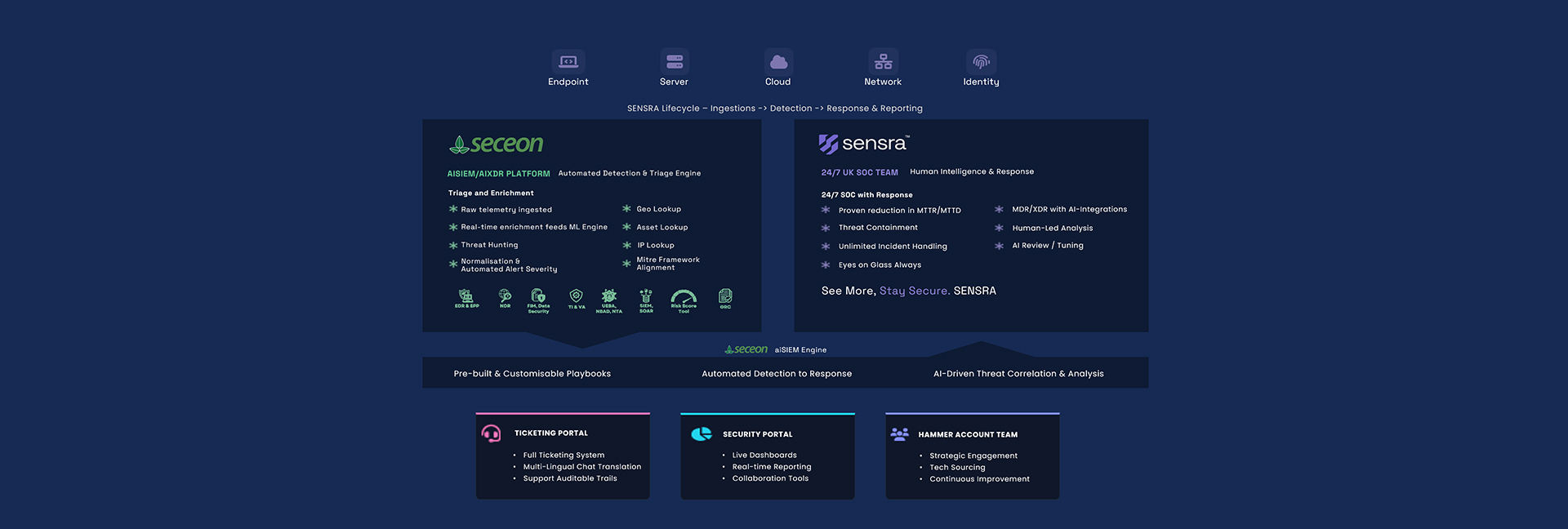
Stay ahead of cyber threats with SENSRA, Hammer’s next-generation Security Operations Centre (SOC) platform. Designed for modern businesses facing complex security challenges, SENSRA delivers unified protection, 24/7 expert monitoring, and rapid response - all in one powerful, easy-to-deploy service.
Whether you need to meet compliance requirements, reduce risk, or free up your IT team, SENSRA gives you the confidence and control to focus on what matters most: your business.
AI/ML-based threat detection
Log ingestion and normalisation
Threat intelligence feeds
SOAR automation and custom runbooks

SENSRA provides real-time monitoring across all environments, including cloud, on-premises, and endpoints, to detect potential threats as they arise.
Alerts are then validated, analysed, and prioritised by our expert team, ensuring that every incident receives the attention it deserves.
When a threat is identified, it is swiftly contained, fully documented, and systems are restored to normal operation.
After each incident, our team conducts a thorough review to continuously strengthen your security posture and improve future response.